Editor’s Note: This is a guest post by Ryan C. Maness of the University of Illinois at Chicago and Brandon Valeriano of the University of Glasgow.
In the rush to note the changing face of the battlefield, few scholars have actually examined the impact of cyber conflict on foreign policy dynamics. Instead most studies are of a hyperbolic nature that suggests the wide ranging impact of cyber conflict on daily social and military life. Here we attempt to cut through the bluff and bluster to examine exactly what happens between countries when cyber conflict is utilized as a foreign policy choice using week events data.
In our previous work we noted that while cyber conflict is proliferating, the level of attacks remains minimal when compared to actual state capabilities and general expectations. Using our dataset of cyber incidents and disputes, we measure the level of conflict and cooperation observed after a cyber incident and dispute to understand the true impact of this new tactic on foreign policy dynamics.
Our work on cyber conflict focuses on rivals which are basically active and historic enemies. It would be thought that during a rivalry, a situation of constant and historic animosity exists, a state will do all it can to harm the other side. If a rival uses a cyber operation to harm its enemy, the likely response should be characterized by further conflictual relations. We therefore expect that cyber incidents and disputes will lead to an escalation of hostility between rivals.
Here we use the events data methodology which measures any interaction, from the smallest diplomatic exchange to the invasion of a country, between two states over time as the dependent variable, an interval measure of conflict and cooperation. Notice and usage of events data has been exploding recently with the release of the GDELT dataset. We support this increased usage of the new data but commissioned our own events dataset prior to the release of GDELT data in order to complete our cyber manuscript and various papers.
The return to the usage of events data is an important step in our field. Bringing cooperation and conflict into the equation allows us to measure rivalry intensity. We commissioned an events dataset that compiles conflict-cooperation scores between dyads that also use cyber tactics as a foreign policy tool from the years 2001 to 2011 with a week being the unit of analysis. Our independent variables come from our dataset that lists all cyber conflict among rival states. In our book in preparation, we go over the results in detail with the methodology and coding decisions fully detailed, but for now it might be useful to point out the basic findings and implications our work since the topic is so important and timely.
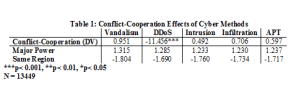
Overall, cyber-incidents and the nature of their targets do not have statistically significant effects on foreign policy interactions if examined according to interaction types. Without statistical significance, it is tough to have confidence that the impact is not random. Table 1 shows the effects of the different methods of cyber conflict states have used against each other from 2001 to 2011. Distributed denial of service (DDoS) methods have statistically significant and negative effects on the conflict cooperation dynamics between rival states. This is surprising due to the low level of severity, as well as the usual short durations of denial of service methods. The actual effect of these attacks is trivial, but the perception and fear associated with these attacks can be amplified given the impact. DDoS methods, therefore, have a psychological effect on many people which leads to aggressive responses by the targeted state. Although rather benign in terms of long-term damage, denial of service methods evoke strong and negative reactions. In contrast more potentially dangerous forms of cyber attack like infiltrations have no significant impact on the foreign policy relationship between states.
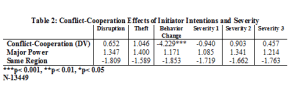
Table 2 displays the effects of cyber incidents coded for the intentions of the initiators as well as severity levels. The effects of these coded explanatory variables are insignificant, except for when the initiator’s intent is to change the behavior of the target state. Whether the tactic is diplomatic, military, or even in cyberspace, states do not like being told what to do, and how to conduct their foreign policy.
Looking at the specific impact of cyber incidents at country to country relations produces some interesting findings. Regional rivals, most with ongoing territorial disputes, react negatively to cyber operations, but non-regional attacks tend to produce little impact on conflict and cooperation levels. The outlier here is China, as when the Chinese use these tactics, the United States and Japan react positively. This demonstrates the actual policy of the United States to respond to these attacks diplomatically, and not with raised escalatory intent.
Overall, we find statistically that only one method of attack, denial of service (DDoS), affects conflict-cooperation dynamics between states. The effect is negative, which means that these methods sour relations between pairs of states when they are utilized as a foreign policy tool. Our results also indicate that when a state uses a cyber attack to affect a behavior change in the target state, the impact is negative. We also find that regional powers and dyads containing the United States have important conflict-cooperation effects when cyber incidents and disputes are involved. The latter effects are all negative, except for one pair of states; the United States and China. When China uses cyber conflict directed towards the United States, the U.S. will respond with diplomacy and try to improve relations with the rising power. The tone of the actual foreign policy context of relations matches that process, with the US even going so far as to never publicly implicate the Chinese state in the attacks and only suggesting that China get a handle of its hackers.
By and large, most cyber operations are allowed to occur with little repercussions. In fact, attacks between great powers like the U.S. and China actually result in positive relations rather than further degenerative interactions. The reason for this is likely because cyber incidents fall below the normal range of hostile operations. They generally are silent and focused attacks; meant to not upset the delicate balance of relations between competing rival states. When China attacked the United States, the U.S. responded diplomatically without further cyber operations. The future could be different, but for now, powers have learned to manage relationships even during constant and harmful cyber operations. This is obviously a surprising and interesting finding given the extremely negative tone of the cyber debate and the extreme warnings by policy makers. We call for more data analysis and a nuanced approach to cyber threats given the increasing amount of evidence we have found regarding the lack of severe cyber threats and lack of escalatory responses in the cyber domain.
Jon Western has spent the last fifteen years teaching IR in liberal arts colleges at Mount Holyoke College and the Five Colleges in western Massachusetts. He has an eclectic range of intellectual interests but often writes on international security, U.S. foreign policy, military intervention, and human rights. He occasionally shares his thoughts about professional life in liberal arts colleges. In his spare time he coaches middle school soccer, mentors the local high school robotics team, skis, and sails.


I dont think that the attacks or DDoS have been big enough or caused a catastrophic collapse. if an event was to literally shut down the NASDAQ, Borse, Wall Street or critical infrastructure like electricity and the internet itself, there would be significant FP action. For example, the Russians completely shut down Latvia a fews ago and they did the same in 2008 in Georgia. If one of the players was to do something similar to a bigger state the dynamics would change considerably
Latvia?
or Estonia? I hadn’t heard of the Latvian attacks.