This post is the first in a four part symposium on the Cuban Missile Crisis, one of the the most studied cases of IR. With the release of documents in recent decades, historical revisions have challenged the received wisdom informed by mainstream...


This post is the first in a four part symposium on the Cuban Missile Crisis, one of the the most studied cases of IR. With the release of documents in recent decades, historical revisions have challenged the received wisdom informed by mainstream...

Earlier this week, Mustafa Kassem, an American held in Egypt, died. The Trump Administration did little to help him. That wasn't surprising. What was surprising was that the international religious...
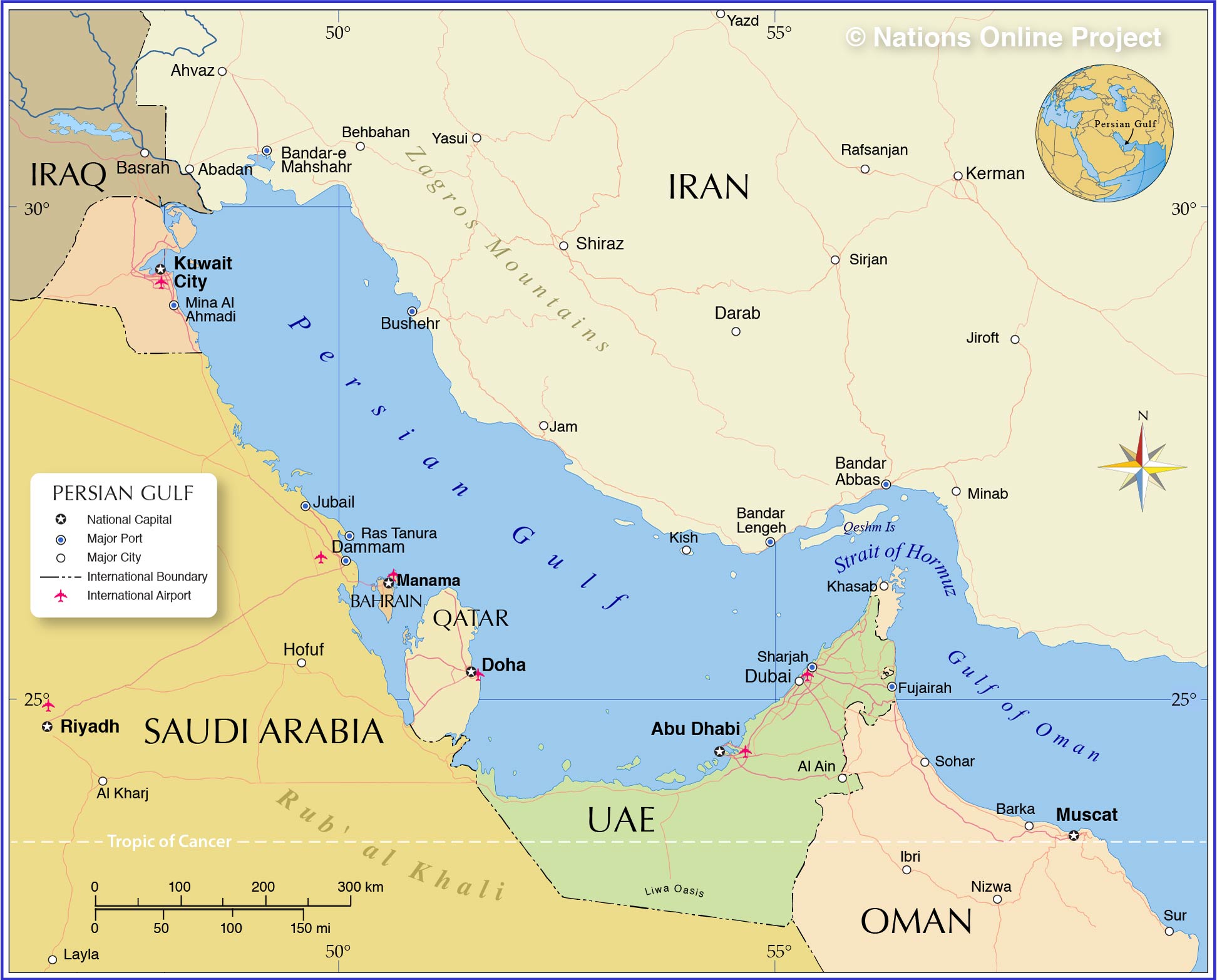
We've all spent the weekend processing the killing of Iranian official Qassim Suleimani by a US airstrike. While this is obviously very important, we should think about a secondary implication of...

Depending on your Twitter addiction, you either went to sleep or woke up with the news that America had assassinated Qassim Suleimani, the commander of Iran's Quds force. Suleimani was one of the...
As a new Duck, who (like Cai & Tom) took a while to consider what to blog about, I finally decided - long-winded academic that I am - to write a series of posts on the #BringBackOurGirls hashtag campaign. To this end, I draw on materials for a keynote I just delivered at the University of Surrey's Center for International Intervention's conference on "Narratives of Intervention: Perspectives from North and South" (#cii2015). Here I go: On April 14, 2014, 276 girls between the ages of 15-18 years were abducted from a school in Chibok, Northern Nigeria, days before they were set to take...
I woke up this morning to read (a few hours behind most of you...one of the few downsides to living in the Pacific Northwest is living behind the news cycle!) about the finalizing of a nuclear deal between the E3/EU+3 and Iran. I'll leave it to others to analyze whether the deal is a good one and whether it will indeed limit the ability of Iran to develop a nuclear weapon. Charles Krauthammer hates it. Joe Cirincione loves it. Jeffery Goldberg isn't quite sure what he thinks of it. My own thinking tends towards agreeing that the agreement isn't spectacular, but that it might be the least...

In late May, the People’s Republic of China (PRC) released a white paper on China’s Military Strategy. This public release is the first of its kind, and it has received relatively little attention in the broader media. While much of the strategy is of no big surprise (broad and sweeping claims to reunification of Taiwan with mainland China, China’s rights to territorial integrity, self-defense of “China’s reefs and islands,” a nod to “provocative actions” by some of its “offshore neighbors” (read Japan)), there was one part of the strategy that calls for a little more scrutiny:...

For the past two years, Jon Monten, Jordan Tama, and I have been working with the survey team at the Chicago Council on Global Affairs (Dina Smeltz and Craig Kafura) to revive the leader surveys that the Council used to run alongside their foreign policy opinion surveys of the American public. Because of the expense and the difficulties of getting responses, the Council discontinued those surveys in 2004, leaving academics with really limited options for comparing public and elite attitudes. With the release of a Council report and a recent piece ($, DM me for a PDF) in Foreign Affairs, we...

I have yet to weigh in on the recent hack on the Office of Personnel Management (OPM). Mostly this is due to two reasons. First is the obvious one for an academic: it is summer! But the second, well, that is due to the fact that as most cyber events go, this one continues to unfold. When we learned of the OPM hack earlier this month, the initial figures were 4 million records. That is, 4 million present and former government employees’ personal records were compromised. This week, we’ve learned that it is more like 18 million. While some argue that this hack is not something to be...

With much attention being given to the passage of the 2015 USA Freedom Act, there is some odd silence about what the bill actually contains. Pundits from every corner identify the demise of section 215 of the Patriot Act (the section that permits the government to acquire and obtain bulk telephony meta data). While the bill does in fact do this, now requiring a “specific selection term” to be utilized instead of bulk general trolling, and it hands over the holding of such data to the agents who hold it anyway (the private companies). Indeed, the new Freedom Act even “permits” amicus curiae...

The Department of Defense’s (DoD) new Cyber Strategy is a refinement of past attempts at codifying and understanding the “new terrain” of cybersecurity threats to the United States. While I actually applaud many of the acknowledgements in the new Strategy, I am still highly skeptical of the DoD’s ability to translate words to deeds. In particular, I am so because the entire Strategy is premised on the fact that the “DoD cannot defend every network and system against every kind of intrusion” because the “total network attack surface is too large to defend against all threats and too vast to...

This past week I was invited to speak as an expert at the United Nations Informal Meeting of Experts under the auspices of the Convention on Certain Conventional Weapons (CCW). The CCW’s purpose is to limit or prohibit certain conventional weapons that are excessively injurious or have indiscriminate effects. The Convention has five additional protocols banning particular weapons, such as blinding lasers and cluster bombs. Last week’s meetings was focused on whether the member states ought to consider a possible sixth additional protocol on lethal autonomous weapons or “killer robots.” My...